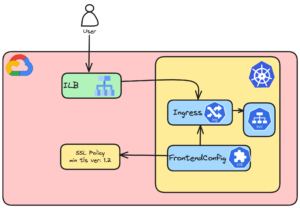
In this Blog, We are going to enforce the Google Kubernetes Engine(GKE) Load balancers to use TLS1.2 or above. As we know TLS 1.0 and TLS 1.1 are deprecated, We are going to create sslpolicy to use TLS1.2 and above.
SSL Policy is created on the GCP project level and will be referenced inside GKE under FrontendConfig CRD. Here we are going to create SSL Policy, FrontendConfig, Ingress and how to test using curl
Steps:
1) Lets create SSL policy on GCP project level
To create SSL policy we are going to specify profile, minimum TLS version and we can create global or regional SSL policy.
There are already three pre-configured profiles in SSL policy:
- COMPATIBLE – Allows the broadest set of clients, including clients that support only out-of-date SSL features, to negotiate SSL with the load balancer.
- MODERN – Supports a wide set of SSL features, allowing modern clients to negotiate SSL.
- RESTRICTED – Supports a reduced set of SSL features, intended to meet stricter compliance requirements.
we can also create CUSTOM profile with multiple SSL features
Now we are going to create global SSL Policy with MODERN profile:
gcloud compute ssl-policies create <ssl-policy-name> \ --profile MODERN \ --min-tls-version 1.2
Lets validate the SSL policy creation in GCP project by executing the below command:
gcloud compute ssl-policies list --global --project=<your_GCP_project>
Reference: https://cloud.google.com/load-balancing/docs/use-ssl-policies#gcloud
2) Now SSL policy is created, we will use the created ssl policy in the GKE ingress by creating FrontendConfig CRD
cat > myfrontendconfig.yaml << EOF apiVersion: networking.gke.io/v1beta1 kind: FrontendConfig metadata: name: my-frontend-config spec: sslPolicy: <ssl-policy-name> EOF
Execute the below command after authenticated to your kubernetes cluster to create FrontendConfig CRD
kubectl apply -f myfrontendconfig.yaml
Reference: https://cloud.google.com/kubernetes-engine/docs/how-to/ingress-configuration#ssl
3) Now we have referenced the ssl policy in FrontendConfig CRD, to apply SSL Policy to the GKE loadbalancer, we need to relate the ingress and frontendconfig.
cat > app-ingress.yaml << EOF
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: application-ingress
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /
nginx.ingress.kubernetes.io/ssl-redirect: "true"
networking.gke.io/v1beta1.FrontendConfig: "my-frontend-config"
spec:
rules:
- host: "foo.bar.com"
http:
paths:
- pathType: Prefix
path: "/bar"
backend:
service:
name: service1
port:
number: 8085
EOF
To create ingress, execute the below command:
kubectl apply -f app-ingress.yaml
4) Now you have enforced your GKE load balancer to use TLS1.2 and above. But how you will test it?
Here is the simple curl command to test your application endpoint:
Validate with TLS1.0:
curl -Iv --tls-max 1.0 https://foo.bar.com
Validate withTTLS1.1:
curl -Iv --tls-max 1.1 https://foo.bar.com
Validate with TLS1.2:
curl -Iv --tls-max 1.2 https://foo.bar.com
Now you will get error for TLS 1.0 and 1.1 because we have enforced to use TLS1.2 and above.